One of the most alluring features of Vangaea is its ability to provide single sign-on access for developers working with multiple hypervisor implementations, such as Microsoft Hyper-V, VMware ESX, Citrix XenServer, etc.
Single Sign-On Flow-Chart
Here is a flow-chart explaining how Vangaea's single sign-on works:
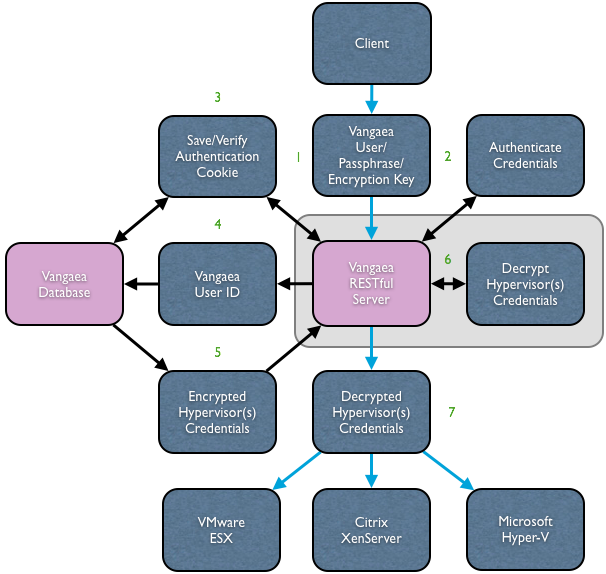
Before I explain the flow chart, there a few things to note:
- The blue connector lines represent a secure communications channel, SSL for example.
- The translucent gray box surrounding the two elements taking part in step 6 represents an "in-memory" action.
Now onto the explanation!
- The client transmits a Vangaea user name and encryption key to the Vangaea server over SSL.
The encryption key can be set in a cookie, com.hyper9.vangaea.key, or it can be sent as a GET parameter, d. It is NOT recommended to transmit the key as a GET parameter for any purpose other than debugging as doing so is entirely not secure.
If there is no authentication cookie present then Vangaea proceeds to step 2. If an authentication cookie is present then Vangaea proceeds to step 3.
- The Java servlet container hosting the Vangaea application or the web server optionally sitting in front of the servlet container MUST guard the URI /r/login in order to force authentication using the given credentials. It does not matter what method is used to authenticate the credentials -- BASIC, FORMS, etc.
- If the request was unauthenticated then at this point a new authentication cookie is generated for the user and saved in the Vangaea database.
If the request was already authenticated then at this point the given authentication cookie is compared to the one that should be saved in the database and if they do not match for the given user ID then the user is forced to log in again.
- The Vangaea database is queried with the ID of the authenticated.
- A set of the user's encrypted hypervisor credentials are returned to the RESTful server. A user may have several sets of hypervisor credentials, one set per hypervisor registered in Vangaea. It is important to note that the user's name, passphrase, and possible certificate are all encrypted in the database and never transmitted in the clear.
- In memory, Vangaea decrypts the user's hypervisor credentials
- Vangaea then sends the decrypted hypervisor credentials, along with the data request, to the intended hypervisors.

